ManageEngine ServiceDesk Plus 9.3
July 15, 2024 · 302 words · 2 min
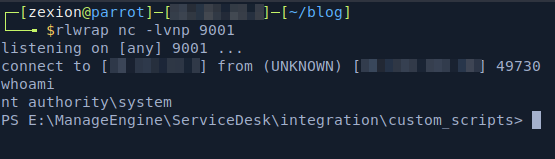
Chaining username enumeration to login as administrator or any administrative role user for reverse shell from scheduled task.
Not a new technique, but found it quite interesting.
CVE-2019-10273
CVE-2019-10273 is a information leakage vulnerability within the ManageEngine ServiceDesk Plus 9.3 software, this vulnerability allows for the enumeration of active users that are registered on the ServiceDesk 9.3 hosted software.
Attack Narrative
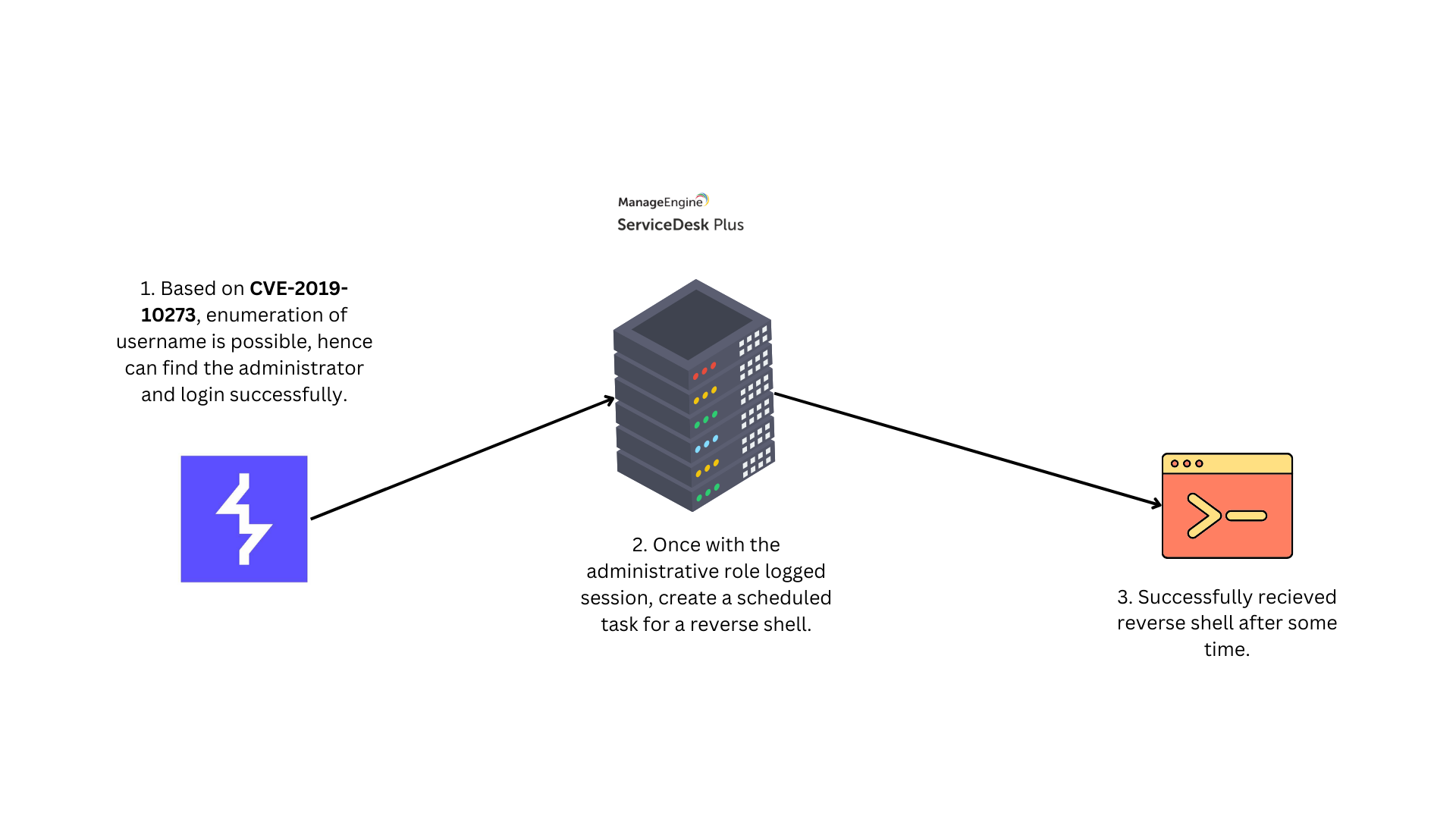
We first exploit a username enumeration vulnerability to identify valid admin usernames. We then use brute force to crack the password and log in as an administrator. With admin access, we schedule a task to execute a reverse shell, gaining full control of the system.
Procedure
1. Getting administrator in the portal.
Upon visiting the ManageEngine ServiceDesk Plus webview, we find ourself in a login panel.
Now just follow the CVE to get yourself a admin role user login session, in this case the username is administrator.
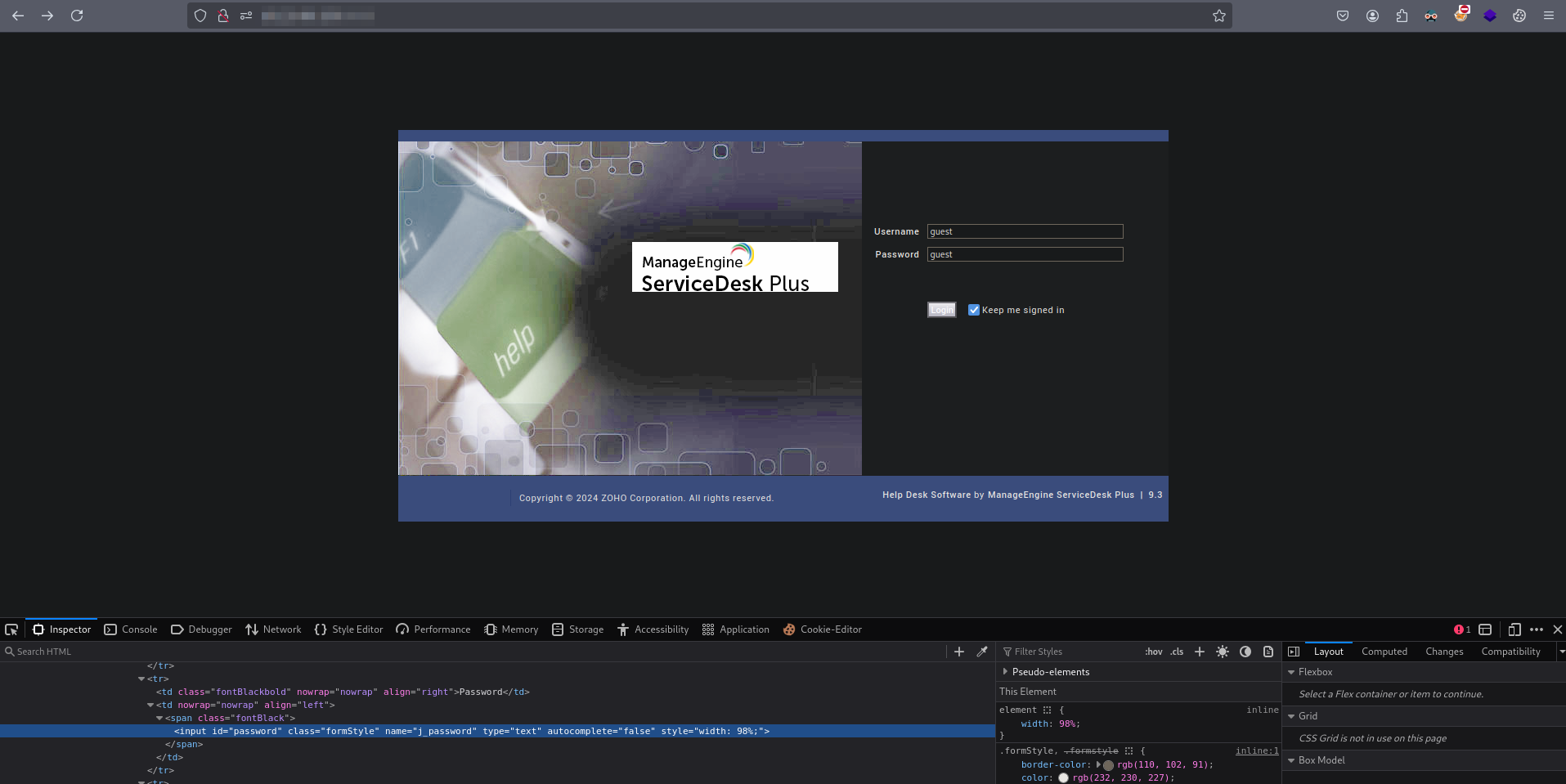
Initially you’d need to login as guest, the credential should be guest:guest. Now in some cases, this might be disabled, so just weep about it then.
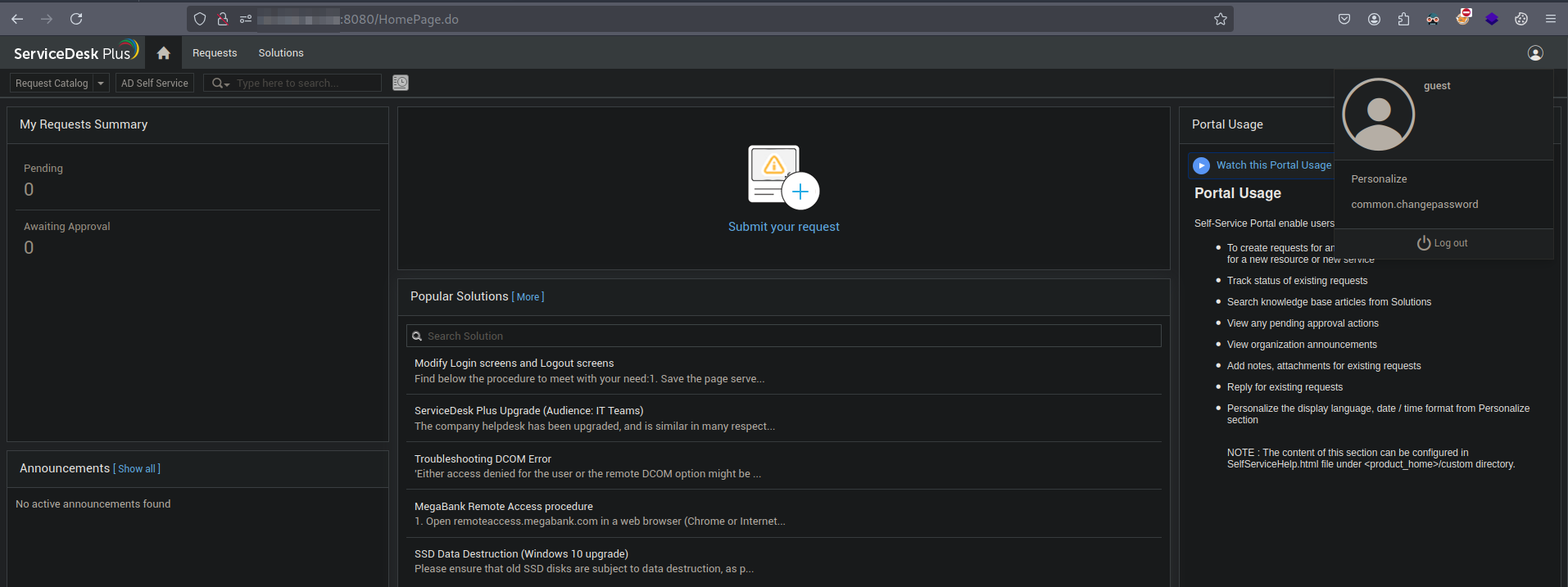
Go to http://192.168.220.13:8080/mc, you should be automatically logged in as guest user from previous login. (Obviously different IP Address.)
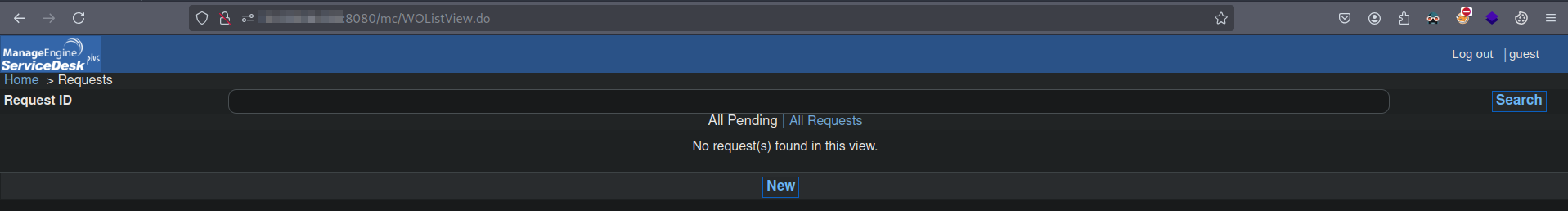
Logout from the /mc, and now you can start your bruteforce for usernames. The password doesn’t have to valid at all. Not going to showcase the bruteforce, configured the server myself, so I know its administrator.
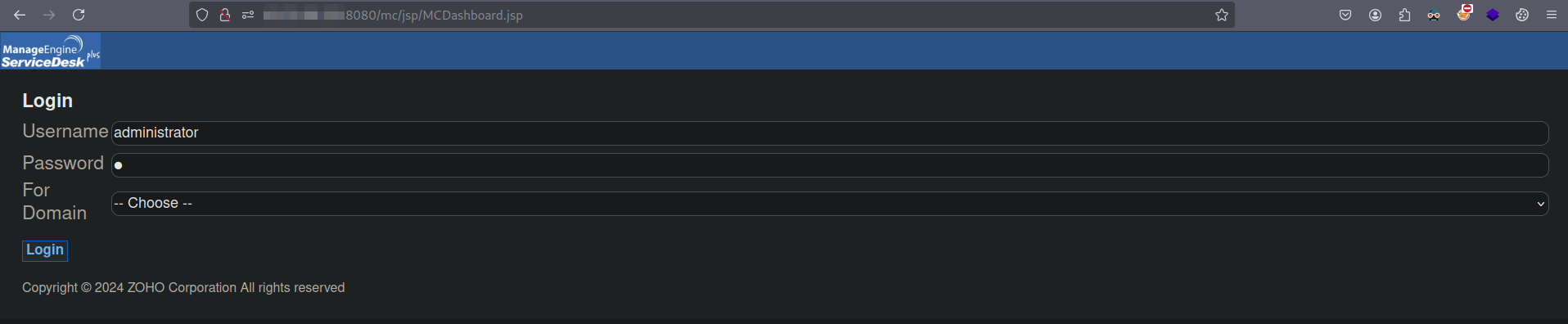
Any invalid password works here.
2. Reverse shell from scheduled tasks.
Observe the Custom Schedules under Admin -> General Settings -> Custom Schedules.
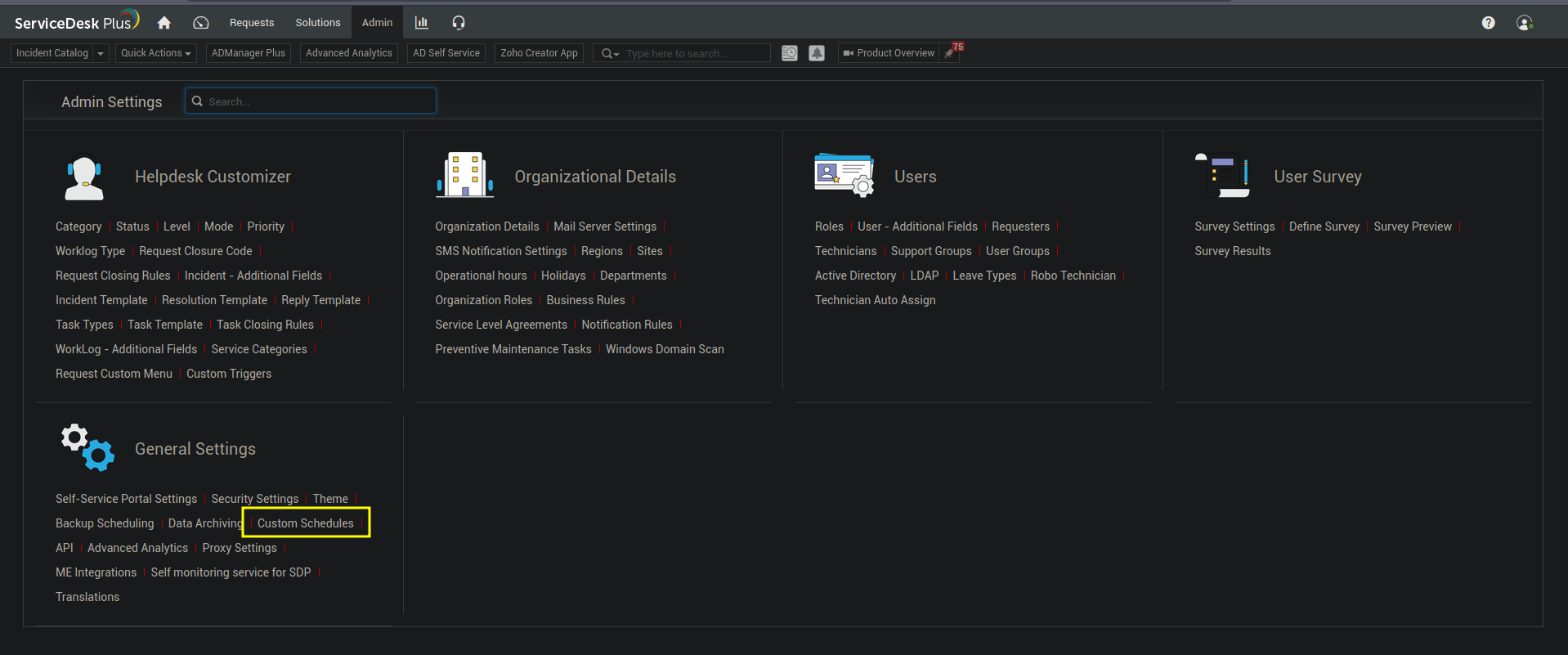
Something like this should be observed where you should be able to create a new custom schedules.
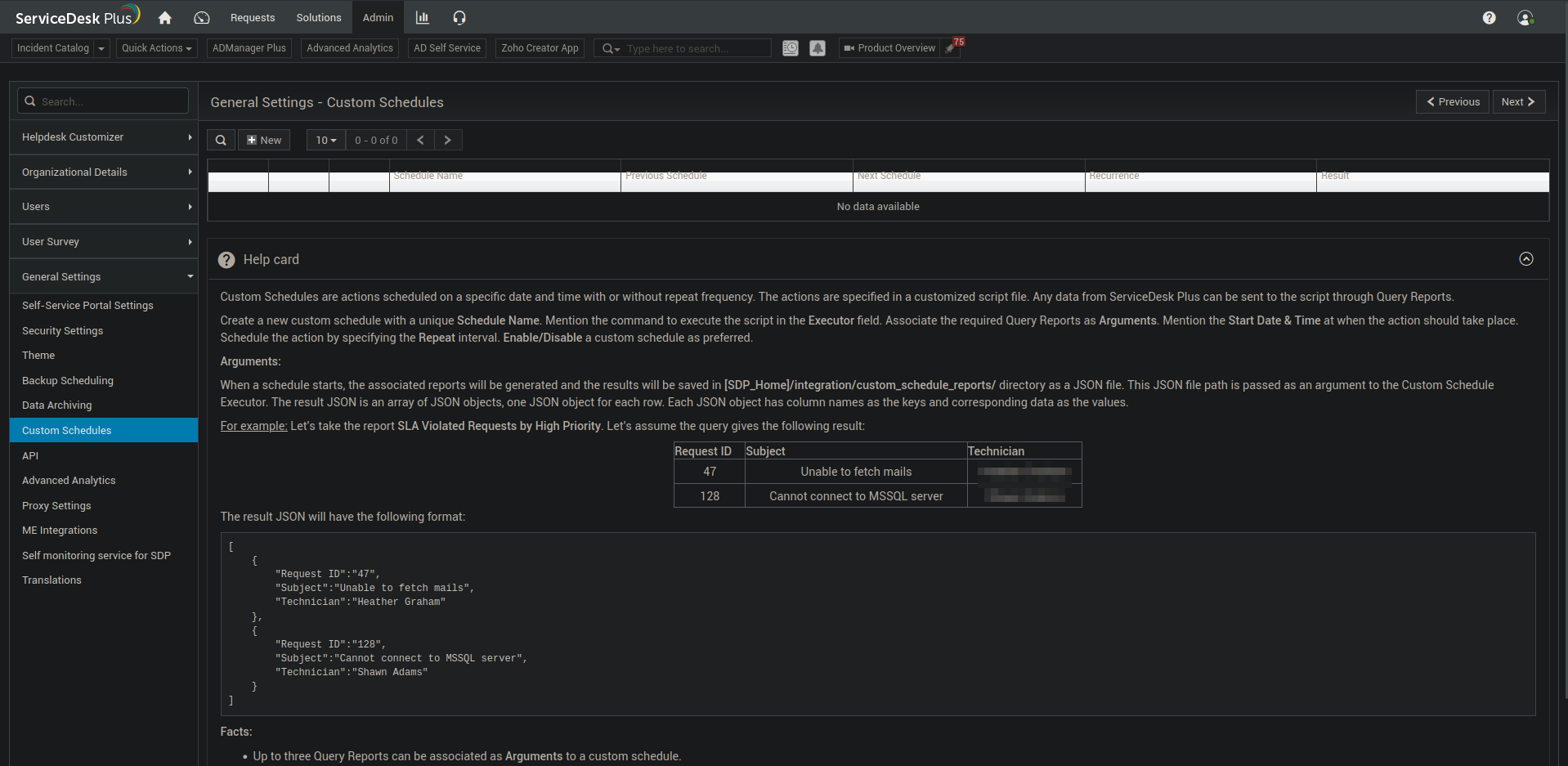
Create a new schedule task, and add a minute later from now for sure causes.
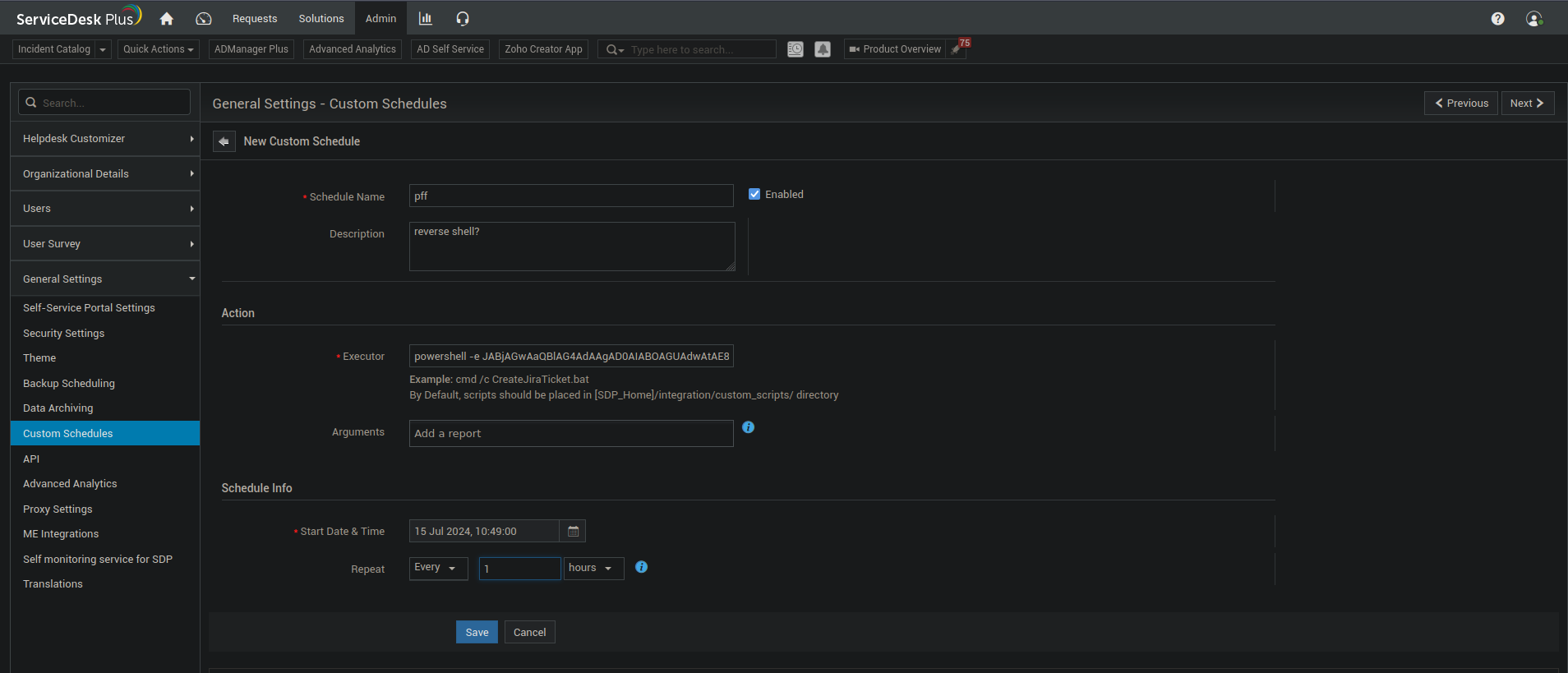
After few minutes, a reverse shell connection should be there.